Latest CompTIA IT Fundamentals fc0-u51 exam practice, fc0-u51 exam dumps free sharing
Certfans is a blog that shares free exam dumps, we update all year round, and we help all friends who need to
open the door to learning. Latest CompTIA IT Fundamentals fc0-u51 exam dumps from pass4itsure CompTIA experts,
free online fc0-u51 exam exercises and fc0-u51 PDF downloads, If you want to pass the fc0-u51 exam
for the first time, please select the full and effective fc0-u51 questions and answers.
https://www.pass4itsure.com/fc0-u51.html provides PDF + VCE mode to help you easily get a certificate
[PDF] Free CompTIA IT Fundamentals fc0-u51 dumps download from Google Drive:
https://drive.google.com/open?id=135qa959b_ggHaW1OYX-bCf0XPF29QPaJ
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
IT Fundamentals+ Certification | CompTIA IT Certifications: https://certification.comptia.org/certifications/it-fundamentals
Pass4itsure offers the latest CompTIA IT Fundamentals fc0-u51 practice test free of charge (50Q&As)
QUESTION 1
Which of the following is an example of ransomware?
A. A user is asked to pay a fee for a password to unlock access to their files.
B. A user receives an email demanding payment for a trial application that has stopped working.
C. A user has opened an Internet browser and is taken to a site that is not the normal home page.
D. A user is asked to open an attachment that verifies the price of an item that was not ordered.
Correct Answer: A
Explanation
QUESTION 2
Which of the following is the BEST example of productivity software?
A. Word processing software
B. Entertainment software
C. Image editing software
D. Anti-malware software
Correct Answer: A
Explanation
QUESTION 3
Which of the following printers requires a special type of paper in order to print?
A. Impact
B. Thermal
C. Inkjet
D. Laser
Correct Answer: B
Explanation
QUESTION 4
Which of the following features of a smartphone controls the screen orientation?
A. Gyroscope
B. NFC
C. Accelerometer
D. GPS
Correct Answer: A
Explanation
QUESTION 5
Which of the following is the function of a CPU?
A. Encrypts data for remote transmission
B. Performs data computation
C. Supplies electricity to components
D. Provides storage location for files
Correct Answer: B
Explanation
QUESTION 6
Which of the following allows for the FASTEST printer connections?
A. Bluetooth
B. USB
C. Parallel
D. Serial
Correct Answer: B
Explanation
QUESTION 7
Which of the following is a safety feature of cloud-based backups?
A. Incremental copy of data
B. Local copy of data
C. Offsite storage of data
D. Full backup of PC data
Correct Answer: C
Explanation
QUESTION 8
When setting up a new workstation, which of the following should be configured during the initial OS setup
wizard?
A. Additional software
B. Date and time settings
C. Peripheral devices
D. Security software
Correct Answer: B
Explanation
QUESTION 9
A user is configuring a new wireless router. Which of the following should be done to ensure that
unauthorized changes cannot be made?
A. Change the SSID
B. Change the router’s address
C. Change the administrator password
D. Change the encryption key
Correct Answer: C
Explanation
QUESTION 10
A user has finished setting up a new computer. Now the operating system requires activation, but the user
discovers the computer has no Internet connection.
Which of the following should the user do FIRST?A. Contact technical support.
B. Reboot the computer.
C. Check the Ethernet cable.
D. Review manufacturer’s website.
Correct Answer: C
Explanation
Explanation/Reference:
QUESTION 11
Malware that has an embedded keylogger to capture all of the keystrokes and steal logins is considered:
A. adware
B. spyware
C. ransomware
D. phishing
Correct Answer: B
Explanation
QUESTION 12
Which of the following components are used to store data? (Select TWO).
A. Motherboard
B. RAM
C. CPU
D. GPU
E. SSD
Correct Answer: BE
Explanation
QUESTION 13
A user is setting up an older wireless access point that has only WEP for encryption.
Which of the following additional steps will help to secure the network? (Select TWO).
A. Disable SSID broadcast.
B. Refresh the MAC address.
C. Filter the MAC address.
D. Refresh the IP address.
E. Use CAT6 cables.
Correct Answer: AC
Explanation
Explanation/Reference:
QUESTION 14
A technician is configuring a wireless router for a small office and the business owner would like the
wireless network to be secured using the strongest encryption possible.
Which of the following should the technician choose?A. WPA2
B. WAP
C. WPA
D. WEP
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 15
A user, Ann, receives a call asking for her password to troubleshoot a problem.
Which of the following describes this type of security threat?
A. Malware
B. Social engineering
C. Spam
D. Physical security
Correct Answer: B
Explanation
Explanation/Reference:
QUESTION 16
A user is browsing the Internet when suddenly a threatening message appears on screen demanding a
payment in order to avoid the system being disabled.
Which of the following BEST describes this type of malware infection?
A. Ransomware
B. Adware
C. Spyware
D. Virus
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 17
Ann, a user, reports that her computer was working this morning, but now the screen is blank. The power
indicator for the monitor is on. Pressing the space bar or mouse does not fix the problem.
Which of the following is the cause?
A. The monitor power cable is unplugged.
B. The video cable has become disconnected.
C. The video driver is not installed.
D. The operating system has encountered a stop error.
E. The screen saver has activated.
Correct Answer: B
ExplanationExplanation/Reference:
QUESTION 18
Which of the following software types allows for the creation of a single file composed of multiple subfiles,
while at the same time reducing the overall size of the combined elements?
A. Database
B. Document sharing
C. Compression
D. Maintenance
Correct Answer: C
Explanation
QUESTION 19
Which of the following are secure network protocols? (Select TWO).
A. IMAP
B. FTPS
C. SMTP
D. HTTPS
E. DNS
Correct Answer: BD
Explanation
QUESTION 20
Which of the following has the lowest latency?
A. SSD
B. NAS
C. Blu-Ray
D. DVD
Correct Answer: A
Explanation
QUESTION 21
Which of the following ports support hot swapping?
Each correct answer represents a complete solution. Choose two.
A. USB
B. Parallel
C. Serial
D. IEEE 1394
Correct Answer: AD
Explanation
Explanation/Reference:
USB and IEEE 1394 ports support hot swapping.
What is USB?
Universal Serial Bus (USB) is a high speed bus standard developed by Compaq, IBM, DEC, Intel,Microsoft, NEC, and Northern Telecom. It provides the Plug and Play capability of Windows to external
hardware devices. USB supports hot plugging, which means that a USB device can be installed or
removed while the computer is running. A single USB port can be used to connect up to
127 peripheral devices, such as CD-ROM drives, tape drives, keyboards, scanners etc. USB 1.1 has a
maximum data transfer rate of 12 Mbps, whereas USB 2.0 has a maximum data transfer rate of 480
Mbps. USB 2.0 is fully backward compatible with USB 1.1.
What is IEEE 1394?
Institute of Electrical and Electronics Engineers (IEEE) 1394 is a standard for high-speed serial bus that
provides enhanced PC connectivity for a wide range of devices. These devices include consumer
audiovisual components, traditional PC storage devices, and handheld devices. IEEE 1394 is also known
as Firewire. Answer options C and B are incorrect. Serial and parallel ports do not support hot swapping or
hot plugging.
QUESTION 22
Your customer is using Windows Vista and complains about the quality of picture he is getting on his
monitor. You find that you cannot adjust the refresh rate or the resolution.
What is the most likely cause?
A. The video card is not recognized by Windows.
B. The monitor is not compatible with the video card.
C. The video card has failed.
D. The video card does not have enough video RAM.
Correct Answer: A
Explanation
Explanation/Reference:
When Windows does not recognize the video card, it gives a set of simplified default settings for refresh
rate, resolution, etc.
Answer option B is incorrect. As long as the monitor can plug into the card, it is compatible. Answer option
C is incorrect. If the video card had failed, there would have been no picture at all on the monitor screen.
Answer option D is incorrect. Lack of sufficient video RAM would just prevent certain graphics from being
displayed.
Reference: http://www.technibble.com/troubleshooting-video-cards-problems-and-solutions/
QUESTION 23
Which of the following are touch screen technologies?
Each correct answer represents a complete solution. Choose all that apply.
A. Surface Wave
B. Resistive
C. Transitive
D. Capacitive
Correct Answer: ABD
Explanation
Explanation/Reference:
Touch screen is a computer display screen that is sensitive to human touch. It allows a user to interact
with a computer by touching the icons or graphical buttons on the monitor screen. It is a system that is
designed to help users who have difficulty in using mouse or keyboard and is used with information kiosks,
computer-based training devices etc. A touch screen panel is attached externally to the monitor that is
connected to a serial or Universal Serial Bus (USB) port on a computer. Nowadays, monitors are also
available with built-in touch screen technology. There are three types of touch screen technologies:
1.Resistive
2.Capacitive
3.Surface Wave
Answer option C is incorrect. There is no such touch screen technology as Transitive. Reference: “http://
en.wikipedia.org/wiki/Touchscreen”
QUESTION 24
What is the maximum resolution that SXGA video technology supports?
A. 2560 x 1600
B. 1024 x 768
C. 1280 x 1024
D. 1280 x 720
Correct Answer: C
Explanation
Explanation/Reference:
SXGA stands for Super eXtended Graphics Array. It is a display standard that refers to video adapters.
This standard is an enhancement of the standard XGA resolution developed by IBM. It is capable of
displaying the resolution of 1280 x 1024 pixels. 1280 refers to horizontal pixels, and 1024
refers to vertical pixels.
Answer option D is incorrect. The WXGA video technology supports a maximum resolution of 1280 x
720.
Answer option A is incorrect. The WQXGA video technology supports a maximum resolution of 2560 x
1600.
Answer option B is incorrect. The XGA video technology supports a maximum resolution of 1024 x
768.
Reference: “http://www.computerhope.com/jargon/s/sxga.htm”
QUESTION 25
Under which environmental conditions is the risk of Electrostatic discharge (ESD) the highest?
A. Low temperature
B. High humidity
C. Low humidity
D. High temperature
Correct Answer: C
Explanation
Explanation/Reference:
Low humidity increases the risk of Electrostatic discharge (ESD). Dry air is a poor conductor of electricity
and it increases the risk of ESD. Humidity reduces the risk ESD because water molecules carry static
electric charge away. Clothing, footwear, and flooring material are important considerations in evaluating
the potential for ESD.
To reduce the risk of ESD, you should take the following precautions while installing new hardware:
Work on a tile floor instead of carpeting.
Remove your shoes, if possible, and roll up your shirt’s sleeves. If you set the component down, do not let
the component touch the table before your hand touches the table.
What is ESD?
ESD stands for Electrostatic discharge. The static electricity that we generate everyday creates ESD. If
you walk across a carpet and touch someone, you experience a mild shock. Electrostatic discharge occurs
when the electrostatic charge is transferred from one charged entity to another entity sensitive to that
charge. components. A wrist strap is a wire with a watchband-style strap at one end and a plug or clip on
the other end. The wrist strap plug or clip is connected to the ground or to the piece of equipment being
worked on.
QUESTION 26
Mark has a file named DAT A. TXT on the C. drive on his computer. He wants to set the hidden attribute
on the file.
Which of the following commands will he use to accomplish this task?
A. ATTRIB +h DATA.TXT
B. ATTRIB -h DATA.TXTC. ATTRIB -A DATA.TXT
D. ATTRIB /hidden DATA.TXT
Correct Answer: A
Explanation
Explanation/Reference:
In order to set the hidden attribute on the file, Mark will have to run the following command on the
command prompt:
ATTRIB +h DATA.TXT
Where:
+ is used for setting attribute.
h is used for hidden attribute.
DATA.TXT is the file name.
Answer option B is incorrect. This is used to clear the hidden attribute from a file. Answer option D is
incorrect. The /hidden is not a valid switch for the ATTRIB command. Answer option C is incorrect. The
ATTRIB -A DATA.TXT command will be used to clear the archive attribute from a file.
Reference: “http://www.computerhope.com/attribhl.htm”
QUESTION 27
Which of the following are removable storage devices/media?
Each correct answer represents a complete solution. Choose three.
A. CD-ROM
B. SD card
C. Hard disk drive
D. USB Pen drive
Correct Answer: ABD
Explanation
Explanation/Reference:
CD-ROM, SD card, USB Pen drive, floppy disk, etc., are removable storage media. CD-ROM (Compact
Disc Read-Only Memory) is a type of removable storage optical media. It can store up to 1GB of data,
although most common CD-ROMs store 700MB of data. It comes in a standard size and format, so users
can load any type of CD-ROM into any CD drive or CD-ROM player. Once data is written to a CD-ROM, it
cannot be erased or changed. SD card is a removable storage device. Secure Digital (SD) card is a non-
volatile memory card format used in portable devices such as mobile phones, digital cameras, and
handheld computers. SD cards are based on the older MultiMediaCard (MMC) format, but they are a little
thicker than MMC cards. Generally an SD card offers a write-protect switch on its side. SD cards generally
measure 32 mm x 24 mm x 2.1 mm, but they can be as thin as 1.4 mm. The devices that have SD card
slots can use the thinner MMC cards, but the standard SD cards will not fit into the thinner MMC slots.
Some SD cards are also available with a USB connector. SD card readers allow SD cards to be accessed
via many connectivity ports such as USB, FireWire, and the common parallel port. USB Pen drive is a
removable storage device. A pen drive is also known as a USB flash drive. It is a small device used to
transfer data from one computer to another through USB ports. Pen drives are available in various
capacities. When a pen drive is plugged into the USB port, Windows Explorer shows it as a removable
drive.
Answer option C is incorrect. The hard disk drive is not a removable storage media. It is installed inside the
computer case. It can store large amounts of data and provides fast read/write performance. HDD can be
connected to a computer with the Integrated Device Electronics (IDE),
Small Computer System Interface (SCSI), and SATA interface. It consists of inflexible platters coated with
material in which data is recorded magnetically with read/write heads. Note: Only external hard disk drives
are removable devices.
QUESTION 28
Which of the following is a framework for defining reusable software components that perform a particular
function or a set of functions in Microsoft Windows?
A. SSIDB. ActiveX
C. Cookies
D. JavaScript
Correct Answer: B
Explanation
Explanation/Reference:
ActiveX is a framework for defining reusable software components that perform a particular function or a
set of functions in Microsoft Windows. ActiveX controls are software components that can be integrated
into Web pages and applications, within a computer or among computers in a network, to reuse the
functionality. Reusability of controls reduces development time of applications and improves program
interfaces. They enhance the Web pages with formatting features and animation. ActiveX controls can be
used in applications written in different programming languages that recognize Microsoft’s Component
Object Model (COM). These controls always run in a container. ActiveX controls simplify and automate the
authoring tasks, display data, and add functionality to Web pages. Answer option D is incorrect. JavaScript
is a simple, light weight, and dynamic World Wide Web (WWW) scripting language developed by Netscape
Communications. The syntax of JavaScript resembles that of C++. JavaScript facilitates integration of
HTML documents, Web components, and multimedia plug-ins. It also aids in the development of server-
side Web applications.
Answer option A is incorrect. SSID stands for Service Set Identifier. It is used to identify a wireless
network. SSIDs are case sensitive text strings and have a maximum length of 32 characters. All wireless
devices on a wireless network must have the same SSID in order to communicate with each other.
Answer option C is incorrect. A cookie is a small bit of text that accompanies requests and pages as they
move between Web servers and browsers. It contains information that is read by a Web application,
whenever a user visits a site. Cookies are stored in the memory or hard disk of client computers. A Web
site stores information, such as user preferences and settings in a cookie. This information helps in
providing customized services to users. There is absolutely no way a Web server can access any private
information about a user or his computer through cookies, unless a user provides the information. A Web
server cannot access cookies created by other Web servers. Reference: “http://en.wikipedia.org/wiki/
ActiveX ”
QUESTION 29
Which of the following will you use to clean your laptop screen?
Each correct answer represents a complete solution. Choose two.
A. Detergent
B. Slightly wet and soft cloth
C. Rough cloth
D. LCD screen cleaner
Correct Answer: BD
Explanation
Explanation/Reference:
In order to clean your laptop screen, you will have to use a slightly wet and soft cloth and a cleaner that is
specially designed for LCD screens. LCD screen cleaner can be purchased from computer shops.
Answer option A is incorrect. Detergent should not be used to clean LCD screens. Detergent contains
chemicals that are harmful for LCD screens. Answer option C is incorrect. Rough cloth should not be used
to clean LCD screens. It will scratch the coating on an LCD screen.
Reference: “http://www.computerhope.com/cleaning.htm#91”
QUESTION 30
Which of the following statements about Hardware Compatibility List (HCL) are true?
Each correct answer represents a part of the solution. Choose two.
A. It ensures that a computer and its components are compatible with the operating system before the
operating system is installed.
B. It contains the listing of all the hardware that operating systems vendors have tested with theiroperating systems.
C. It ensures that a computer and its components are working properly.
D. It contains the license to use operating systems.
Correct Answer: AB
Explanation
Explanation/Reference:
The Hardware Compatibility List (HCL) contains the listing of all the hardware that operating systems
vendors have tested with their operating systems. Through HCL, an administrator can be sure that a
computer and its components are compatible with the operating system before the operating system is
installed. HCL helps administrators to verify that the CPU, RAM, storage devices, various interface cards,
and other hardware components are supported by the operating systems. Reference: “http://
www.microsoft.com/whdc/hcl/default.mspx”
QUESTION 31
Which of the following statements about Standby Power Supply (SPS) is true?
Each correct answer represents a complete solution. Choose two.
A. It provides protection against power surges.
B. It provides protection against power drops and power surges.
C. It provides no protection against power surges.
D. It provides protection against under voltage.
Correct Answer: CD
Explanation
Explanation/Reference:
An SPS device provides protection against under voltage. When a power drop occurs, it engages battery
power and takes over from power outlets. SPS does not provide protection against power surges.
Answer option B is incorrect. It is the Uninterruptible Power Supply (UPS) that protects devices against
power drops and power surges.
Answer option A is incorrect. Surge protectors protect devices against power surges.
QUESTION 32
You are responsible for tech support at your company. You have been instructed to make certain that all
desktops support file and folder encryption. Which file system should you use when installing
Windows XP?
A. FAT
B. EXT4
C. FAT32
D. NTFS
Correct Answer: D
Explanation
Explanation/Reference:
NTFS is the file system first introduced with Windows 2000 and it inherently supports file encryption as
well as other exciting features such as file compression.
What is NTFS?
NTFS is an advanced file system designed for use specifically in Windows NT, Windows 2000/2003, and
Windows XP operating systems. It supports file system recovery, large storage media, long file names,
and other features. NTFS offers features such as disk quotas, distributed link tracking, compression, and
mounted drives.
NTFS also offers security features, such as encryption and file and folder permissions.
These features are not available on FAT volumes.
Answer options A and C are both incorrect. FAT is an old file system used with DOS and Windows
3.1. FAT32 was simply a 32 bit version of FAT and was used with Windows 95 and Windows 98.Neither FAT nor FAT32 support file or folder encryption. Answer option B is incorrect. EXT is a file system
used with Linux and does not work with any version of Windows.
Reference:
http://www.microsoft.com/windows/windows2000/en/advanced/help/encrypt_overview.htm
QUESTION 33
Which of the following statements about High-Definition Multimedia Interface (HDMI) are true?
Each correct answer represents a complete solution. Choose two.
A. It is capable of delivering the highest quality digital video and multi-channel digital audio on a single
cable.
B. It is an interface primarily used to connect hard disk and CD drives in a computer.
C. It is a new I/O bus technology that has more bandwidth than PCI and AGP slots.
D. It has two types of connectors: Type A and Type B.
Correct Answer: AD
Explanation
Explanation/Reference:
HDMI stands for High-Definition Multimedia Interface. It is a standard, uncompressed, and all-digital audio/
video interface. HDMI is capable of delivering the highest quality digital video and multichannel digital
audio on a single cable. It provides an interface between any audio/video sources, such as a DVD player
or a computer and a digital television (DTV) or video monitor. HDMI transmits all ATSC HDTV standards
and supports 8-channel digital audio, with extra bandwidth to accommodate future enhancements. HDMI
has two types of connectors: Type A and Type B. Type A and Type B connectors use 19 pins and 29 pins,
respectively. The Type B connector is designed for very high-resolution displays that are expected in near
future.
Answer option B is incorrect. Integrated Digital Electronics (IDE) is an interface primarily used to connect
hard disk and CD drives in a computer. Answer option C is incorrect. PCI Express (PCIe), also known as
3rd Generation I/O (3GIO), is a type of computer bus. It is a new I/O bus technology that has more
bandwidth than PCI and AGP slots. It uses two low-voltage differential pairs, at 2.5Gb/s in each direction. It
is designed to replace PCI and AGP expansion slots. The bus is available in several different bus widths:
x1, x2, x4, x8, x12, x16, and x32. PCIe is able to transfer data in both directions at a time. PCIe hardware
will work on operating systems that support PCI.
Reference: “http://en.wikipedia.org/wiki/HDMI”
QUESTION 34
Which of the following technologies is used to detect unauthorized attempts to access and manipulate
computer systems locally or through the Internet or an intranet?
A. Demilitarized zone (DMZ)
B. Firewall
C. Intrusion detection system (IDS)
D. Packet filtering
Correct Answer: C
Explanation
Explanation/Reference:
An Intrusion detection system (IDS) is used to detect unauthorized attempts to access and manipulate
computer systems locally or through the Internet or an intranet. It can detect several types of attacks and
malicious behaviors that can compromise the security of a network and computers. This includes network
attacks against vulnerable services, unauthorized logins and access to sensitive data, and malware (e.g.
viruses, worms, etc.). An IDS also detects attacks that originate from within a system. In most cases, an
IDS has three main components: Sensors, Console, and Engine. Sensors generate security events. A
console is used to alert and control sensors and to monitor events. An engine is used to record events and
to generate security alerts based on received security events. In many IDS implementations, these three
components are combined into a single device. Basically, following two types of IDS are used :
Network-based IDSHost-based IDS
Answer option D is incorrect. Packet filtering is a method that allows or restricts the flow of specific types of
packets to provide security. It analyzes the incoming and outgoing packets and lets them pass or stops
them at a network interface based on the source and destination addresses, ports, or protocols. Packet
filtering provides a way to define precisely which type of IP traffic is allowed to cross the firewall of an
intranet. IP packet filtering is important when users from private intranets connect to public networks, such
as the Internet.
Answer option B is incorrect. A firewall is a tool to provide security to a network. It is used to protect an
internal network or intranet against unauthorized access from the Internet or other outside networks. It
restricts inbound and outbound access and can analyze all traffic between an internal network and the
Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports.
Answer option A is incorrect. Demilitarized zone (DMZ) or perimeter network is a small network that lies in
between the Internet and a private network. It is the boundary between the Internet and an internal
network, usually a combination of firewalls and bastion hosts that are gateways between inside networks
and outside networks. DMZ provides a large enterprise network or corporate network the ability to use the
Internet while still maintaining its security.
Reference: “http://en.wikipedia.org/wiki/Intrusion-detection_system”
QUESTION 35
Which of the following types of SATA hard disk drives is used for the Desktop computers?
A. 3.5 inches
B. 6.2 inches
C. 1.8 inches
D. 2.5 inches
Correct Answer: A
Explanation
Explanation/Reference:
The 3.5 inches SATA hard disk is used for the Desktop computers. The Serial ATA (SATA) computer bus
is a storage-interface for connecting host bus adapters to mass storage devices such as hard disk drives
and optical drives. SATA offers several compelling advantages over the older parallel ATA (PATA)
interface, such as reduced cable-bulk and cost, faster and more efficient data transfer, full duplex, and hot
swapping. It is designed to replace the older ATA (AT Attachment) standard (Parallel ATA). All SATA
devices support hot plugging and hot swapping. SATA supports Native Command Queuing (NCQ) for
enhanced performance.
Answer options C and D are incorrect. The 1.8 inches and 2.5 inches hard disk drives are used in laptops.
Answer option B is incorrect. There is no such size of SATA hard disk drive as 6.2 inches. Reference:
“http://en.wikipedia.org/wiki/Serial_ATA”
QUESTION 36
You are trying to select a particular wireless encryption algorithm. You are concerned that it implements as
much of the wireless 802.11i standard as possible.
Which encryption algorithm should you implement?
A. WEP2
B. WPA2
C. WPA
D. WEP
Correct Answer: B
Explanation
Explanation/Reference:
WPA2 is, to date, the most 802.11i compliant encryption protocol available. Answer option C is incorrect.
WPA2 is an improvement over WPA, but unlike WPA2 it does not implement certain key elements of
802.11i such as Counter Mode with Cipher Block Chaining Message Authentication Code.
Answer option D is incorrect. WEP does not implement many aspects of the 802.11i standards.
What is WEP?Wired Equivalent Privacy (WEP) is a security protocol for wireless local area networks (WLANs). It has two
components, authentication and encryption. It provides security, which is equivalent to wired networks, for
wireless networks. WEP encrypts data on a wireless network by using a fixed secret key. WEP
incorporates a checksum in each frame to provide protection against the attacks that attempt to reveal the
key stream. Answer option A is incorrect. WEP2 does not actually exist. It is not an encryption algorithm.
Reference: http://en.wikipedia.org/wiki/Wi-Fi_Protected_Access
QUESTION 37
Which of the following are used by FireWire 800 devices?
A. 6-pin connectors
B. 10-pin connectors
C. 9-pin connectors
D. 4-pin connectors
Correct Answer: C
Explanation
Explanation/Reference:
FireWire 800 devices use 9-pin connectors at both ends of the cable. FireWire 400 devices can also be
connected to the FireWire 800 ports and vice versa by using an appropriate adapter cable.
What are FireWire ports? Hide
FireWire ports are found on high-end computers and many new media centers. They are also called IEEE
1394 ports.
FireWire ports transfer data at a rate of 400 Mbps or 800 Mbps. They are used primarily for video transfer
from digital movie cameras.
Answer options D and A are incorrect. FireWire 400 devices use 4-pin or 6-pin connectors. Reference:
“http://en.wikipedia.org/wiki/FireWire ”
QUESTION 38
Which of the following types of batteries are considered as environmental hazards?
Each correct answer represents a complete solution. Choose three.
A. Button cell
B. Lead-acid
C. NiMH
D. NiCd
Correct Answer: ABD
Explanation
Explanation/Reference:
The following types of batteries are considered as environmental hazards:
Nickel cadmium (NiCd)
Lead-acid
Button cell
Nickel cadmium (NiCd) batteries contain nickel and cadmium. Cadmium is highly toxic. Lead-acid batteries
contain lead that is considered as environmental hazard. Button cell batteries contain mercury that is
considered as environmental hazard. Answer option C is incorrect. Nickel metal hydride (NiMH) batteries
are not considered as environmental hazards.
Reference: “http://en.wikipedia.org/wiki/Battery_(electricity)”
QUESTION 39
Which of the following slots on a motherboard are best for a video card?
Each correct answer represents a complete solution. Choose two.
A. PCIe
B. PCI
C. AGPD. EISA
Correct Answer: AC
Explanation
Explanation/Reference:
AGP and PCIe are the best slots for a video card. PCI Express (PCIe), also known as 3rd Generation I/O
(3GIO), is a type of computer bus. It is a new I/O bus technology that has more bandwidth than PCI and
AGP slots. It uses two low-voltage differential pairs, at 2.5Gb/s in each direction. It is designed to replace
PCI and AGP expansion slots.
The bus is available in several different bus widths: x1, x2, x4, x8, x12, x16, and x32. PCIe is able to
transfer data in both directions at a time. PCIe hardware will work on operating systems that support PCI.
AGP is a high speed 32-bit bus designed for high performance graphics and video support. It allows a
video card to have direct access to a computer’s RAM, which enables fast video performance. AGP
provides a bandwidth of up to 2,133 MB/second. Answer option D is incorrect. The Extended Industry
Standard Architecture (EISA) is a 32- bit PC expansion bus designed as a superset of a 16-bit ISA bus.
The EISA bus is designed to increase the speed and expand the data width of the legacy expansion bus
while still supporting older ISA cards.
EISA slots are obsolete now.
Answer option B is incorrect. PCIe and AGP slots are better than PCI slot for a video card. Reference:
“http://en.wikipedia.org/wiki/PCI_Express”,
“http://en.wikipedia.org/wiki/Accelerated_Graphics_Port”
QUESTION 40
Which of the following does the image denote?
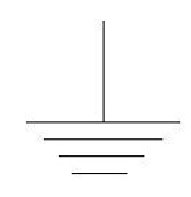
A. Ground
B. Capacitor
C. Resistor
D. Terminator
Correct Answer: A
Explanation
QUESTION 41
Which of the following SCSI types use 16-bit bus?
A. Fast Wide SCSI-2
B. Double Wide SCSI-2
C. Fast SCSI-2
D. Wide SCSI-2
E. Ultra-2 SCSI (Fast-40)
Correct Answer: AD
Explanation
Explanation/Reference:
The following SCSI types use 16-bit bus:
1.Wide SCSI-22.Fast Wide SCSI-2
3.Wide Ultra SCSI-3
4.Wide Ultra-2 SCSI
5.Ultra-3 (Fast-80 or Ultra 160)
Small Computer System Interface (SCSI) is the second most popular drive interface in use today after the
Integrated Drive Electronics (IDE) interface. SCSI is faster than IDE and supports more devices.
SCSI devices, such as hard disk drive and CD-ROM drive, are better suited in a network environment in
which many users access shared drives simultaneously. Answer option B is incorrect. Double Wide SCSI-
2 uses 32-bit bus. Answer options C and E are incorrect. Fast SCSI-2 and Ultra-2 SCSI (Fast-40) used 8-
bit bus.
Reference: “http://en.wikipedia.org/wiki/SCSI”
QUESTION 42
Which of the following hardware uses flash memory technology?
A. PCMCIA card
B. Smart card reader
C. Secure digital card
D. DDR2 SDRAM
Correct Answer: C
Explanation
Explanation/Reference:
Secure Digital (SD) card is a non-volatile memory card format used in portable devices such as mobile
phones, digital cameras, and handheld computers. SD cards are based on the older
MultiMediaCard (MMC) format, but they are a little thicker than MMC cards. Generally an SD card offers a
write-protect switch on its side. SD cards generally measure 32 mm x 24 mm x 2.1 mm, but they can be as
thin as 1.4 mm. The devices that have SD card slots can use the thinner MMC cards, but the standard SD
cards will not fit into the thinner MMC slots. Some SD cards are also available with a USB connector. SD
card readers allow SD cards to be accessed via many connectivity ports such as USB, FireWire, and the
common parallel port. It uses flash memory technology.
Answer option A is incorrect. Personal Computer Memory Card International Association (PCMCIA) card is
also known as PC card. The PC card uses a small expansion slot and is primarily used in laptops.
However, PC cards are also available in some of the desktop computers. It does not use flash memory
technology. Answer option D is incorrect. DDR2 SDRAM is a type of memory module. DDR2 SDRAM is an
enhanced version of DDR SDRAM. It uses a 240-pin memory module and runs at the speed of 400 MHz
or higher. It uses an operating voltage of 1.8 volts, instead of 2.5 volts used in DDR SDRAM. This results
in less power consumption. DDR2 SDRAM transfers 64 bits of data twice every clock cycle.
DDR2 SDRAM memory is not compatible with DDR SDRAM memory slots. Answer option B is incorrect. A
smart card reader is an interface device, which is used to read information from or write information to a
smart card. It does not use flash memory technology.
QUESTION 43
Mark purchases a new computer and installs the Windows 2000 Professional operating system on it.
He wants to connect the computer to the Internet. Which of the following actions can he take to protect his
computer from unauthorized access, adware, and malware?
Each correct answer represents a complete solution. Choose two.
A. Configure a firewall on the computer.
B. Configure auditing on the computer.
C. Set hidden attributes on his important files.
D. Install all the service packs available for the operating system.
Correct Answer: AD
Explanation
Explanation/Reference:
In order to protect his computer from unauthorized access, adware, and malware, Mark can take thefollowing actions:
Install all the service packs available for the operating system.
Configure a firewall on the computer.
What is Service Pack?
A service pack is a collection of Fixes and Patches in a single product. A service pack can be used to
handle a large number of viruses and bugs or to update an operating system with advanced and better
capabilities. A service pack usually contains a number of file replacements.
What is a firewall?
A firewall is a tool to provide security to a network. It is used to protect an internal network or intranet
against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound
access and can analyze all traffic between an internal network and the Internet. Users can configure a
firewall to pass or block packets from specific IP addresses and ports.
Answer option C is incorrect. Setting hidden attributes on files cannot protect computers from unauthorized
access, adware, and malware.
Answer option B is incorrect. Configuring auditing will not protect computers from unauthorized access,
adware, and malware. Auditing is used to track user accounts for file and object access, logon attempts,
system shutdown, etc. This enhances the security of the network.
Reference: TechNet, Contents: ” Chapter 2 – Malware Threats”
QUESTION 44
Which of the following types of attacks entices a user to disclose personal information such as social
security number, bank account details, or credit card number?
A. Password guessing attack
B. Spoofing
C. Phishing
D. Replay attack
Correct Answer: C
Explanation
Explanation/Reference:
Phishing is a type of scam that entice a user to disclose personal information such as social security
number, bank account details, or credit card number. An example of phishing attack is a fraudulent e-mail
that appears to come from a user’s bank asking to change his online banking password. When the user
clicks the link available on the e-mail, it directs him to a phishing site which replicates the original bank
site. The phishing site lures the user to provide his personal information. Answer option B is incorrect.
Spoofing is a technique that makes a transmission appear to have come from an authentic source by
forging the IP address, email address, caller ID, etc. In IP spoofing, a hacker modifies packet headers by
using someone else’s IP address to his identity. However, spoofing cannot be used while surfing the
Internet, chatting on- line, etc. because forging the source
IP address causes the responses to be misdirected. Answer option D is incorrect. Replay attack is a type
of attack in which attackers capture packets containing passwords or digital signatures whenever packets
pass between two hosts on a network.
In an attempt to obtain an authenticated connection, the attackers then resend the captured packet to the
system.
Answer option A is incorrect. A password guessing attack occurs when an unauthorized user tries to log
on repeatedly to a computer or network by guessing usernames and passwords. Many password guessing
programs that attempt to break passwords are available on the Internet. Following are the types of
password guessing attacks:
Brute force attack
Dictionary attack
Reference: “http://en.wikipedia.org/wiki/Phishing”
QUESTION 45
Which of the following devices does SCSI support?
Each correct answer represents a complete solution. Choose all that apply.
A. Tape drive
B. Sound card
C. CD driveD. Modem
E. Hard disk drive
Correct Answer: AC
Explanation
Explanation/Reference:
Small Computer System Interface (SCSI) supports CD drive, tape drive, and hard disk drive.
What is SCSI? Hide
Small Computer System Interface (SCSI) is the second most popular drive interface in use today after the
Integrated Drive
Electronics (IDE) interface. SCSI is faster than IDE and supports more devices. SCSI devices, such as
hard disk drive and CD-ROM drive, are better suited in a network environment in which many users
access shared drives simultaneously. SCSI has three standards: SCSI-1, SCSI-2, and SCSI-3.
Reference: TechNet, Contents: “Storage Management Operations Guide”
QUESTION 46
Which of the following wireless standards has a transmission speed of up to 720 Kbps?
A. Infrared
B. Bluetooth
C. IEEE 802.11a
D. Wi-Fi
Correct Answer: B
Explanation
Explanation/Reference:
Bluetooth is a standard for short-range radio links between laptops, mobile phones, digital cameras, and
other portable devices. Bluetooth devices contain a transceiver chip. The transceiver transmits and
receives data with the frequency of 2.45 GHz. It has transmission speeds of up to 720 Kbps and the
network range of 33 feet. Answer option A is incorrect. Infrared is a communication medium used for
wireless networks to transfer data between devices. Infrared can transmit signals at high rates because of
the high bandwidth of infrared light. An infrared network can normally broadcast at 10 Mbps.
Answer option D is incorrect. The Wi-Fi (802.11b standard) wireless technology is used to offer Internet
access in public places. The 802.11b standard, defined by IEEE, is an extension of the 802.11 standard of
wireless network. It is also referred to as 802.11 High Rate. It operates in 2.4GHz band and brings data
rates up to 11Mbps. Answer option C is incorrect. The maximum data transfer rate of the 802.11a wireless
standard is 54 Mbps.
QUESTION 47
How many pins are available on a PS/2 Mini-DIN connector?
A. 5
B. 4
C. 6
D. 3
Correct Answer: C
Explanation
Explanation/Reference:
A PS/2 Mini-DIN connector has 6-pins , while only four are used. Pin 1 is used for keyboard data signal,
pin 3 is ground, pin 4 has +5 Volt DC, pin 5 is used for keyboard clock, and pins 2 and 6 are not used. The
PS/2 6-pin Mini-DIN connector is used for both keyboard and mouse. Older keyboard connectors use 5-pin
DIN connector.
QUESTION 48
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows- based network.
You do maintenance work on a Windows 2000 Professional computer. You require to perform the
following jobs:Exhaustive disk checking.
Locate bad sectors (if any).
Recover readable information.
Which of the following commands will you use to accomplish the task?
A. CHKDSK /v
B. CHKDSK /i
C. CHKDSK /f
D. CHKDSK /r
Correct Answer: D
Explanation
Explanation/Reference:
In order to accomplish the task, you will have to run the following commanD.
CHKDSK /r
The CHKDSK command verifies the integrity of the hard disk installed on a computer. Using the command
with different parameters can resolve a number of issues, which are described as follows:
SwitchDescription
CHKDSK /f It fixes all the errors on the hard disk of a computer. CHKDSK /vIt displays the full path and
name of every file on the disk. CHKDSK /r It locates bad sectors and recovers readable information.
CHKDSK /l It changes the log file size to the specified number of kilobytes. If the size is not specified, it
displays the current size.
CHKDSK /i It performs a less vigorous check of index entries. CHKDSK /c It skips checking of cycles
within the folder structure. Reference: TechNet, Contents: “Chapter 27 – Troubleshooting Disks and File
Systems”
QUESTION 49
Which of the following statements about Bluetooth are true?
Each correct answer represents a complete solution. Choose two.
A. It forms a network whenever two Bluetooth devices come within a range of ten meters.
B. It has a maximum transmission range of 200 meters.
C. It does not require a line-of-sight connection between devices.
D. It requires a line-of-sight connection between devices.
Correct Answer: AC
Explanation
Explanation/Reference:
Bluetooth is a standard for very low powered and short-range radio connections. As a radio technology, it
does not require a line-of-sight connection as an infrared connection does. Bluetooth is used to link
Personal Digital Assistant (PDA), mobile phones, and laptops, and provides them with Internet access via
hot spots. It uses the 2.4 Ghz spectrums with a data transfer rate of about 1
Mbps. Bluetooth networks are not permanent as compared to other networks where a central
communication point is needed such as a hub or a router. A Bluetooth network can be formed when two
Bluetooth devices are within a range of ten meters, enabling them to communicate directly with each other.
This dynamically created network is known as a piconet. A Bluetooth-enabled device can support up to
seven other Bluetooth devices in a master-slave relationship; the first Bluetooth device is the master, and
all the other devices are slaves that communicate with the master in one piconet. The maximum
transmission range of Bluetooth is around 10 meters.
Answer option D is incorrect. The infrared devices require a line-of-sight connection between devices.
Answer option B is incorrect. The maximum transmission range of Bluetooth is around 10 meters.
Reference: “http://www.bluetooth.com/bluetooth/”
QUESTION 50
You have an older Windows 98 computer. You wish to upgrade to Windows Vista Home Basic. What must
you do?
A. First upgrade to Windows 2000 then upgrade to Vista Home Basic.
B. First upgrade to Windows XP Pro, then upgrade to Vista Home Basic.
C. Simply buy and install the Windows Vista Home Basic Upgrade.
D. First upgrade to Windows XP Home, then upgrade to Vista Home Basic.
Correct Answer: D
Explanation
Explanation/Reference:
You will have to first upgrade to Windows XP home, and then to Vista Home. Answer option C is incorrect.
Windows 98 cannot be directly upgraded to Windows Vista. Answer option B is incorrect. Windows XP
professional cannot be upgraded to Windows Vista Home
Basic, but it can be upgraded to Windows Vista Business or Ultimate. Answer option A is incorrect.
Windows 2000 cannot be upgraded to Windows Vista. Reference: http://support.microsoft.com/kb/931225
About the exam:
The CompTIA IT Fundamentals+ exam focuses on the essential IT skills and knowledge needed to perform tasks commonly
performed by advanced end-users and entry-level IT professionals alike, including:
Using features and functions of common operating systems and establishing network connectivity
Identifying common software applications and their purpose
Using security and web browsing best practices
This exam is intended for candidates who are advanced end users and/or are considering a career in IT.
The exam is also a good fit for individuals interested in pursuing professional-level certifications, such as A+.
Conclusion:
Certfans free share effective CompTIA IT Fundamentals fc0-u51 exam dumps and fc0-u51 pdf download online,
free content can help you unravel a lot of doubts, want to obtain a certificate please choose the full fc0-u51 exam dumps.
Certfans all free content from Pass4itsure experts, we recommend that you choose him and want to obtain a certificate at
once please select https://www.pass4itsure.com/fc0-u51.html PDF + VCE
[PDF] Free CompTIA IT Fundamentals fc0-u51 dumps download from Google Drive:
https://drive.google.com/open?id=135qa959b_ggHaW1OYX-bCf0XPF29QPaJ
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.certfans.com/100-real-cisco-dcict-200-155-dumps-exam/